- Sonarlint For Visual Studio 2019 Full
- Sonarlint Integration With Visual Studio 2019
- Sonarlint Visual Studio 2019 Configuration
SonarLint is available for Visual Studio Code. SonarLint helps you detect and fix quality issues as you write code. Like a spell checker, SonarLint squiggles flaws so they can be fixed before committing code. PVS-Studio is a tool for detecting bugs and security weaknesses in the source code of.
- Starting in Visual Studio 2019 version 16.3, there are two checkboxes available in the Code Analysis properties page that let you control whether analyzers run at build time and design time. These options are project-specific. To open this page, right-click the project node in Solution Explorer and select Properties. Select the Code Analysis tab.
- SonarLint is integrated with Microsoft Code Analysis framework, so rules for C# and VB.NET can be fine-tuned in the. Ruleset file used by your project. The set of active rules can also be tuned for JavaScript, C and C. Find logs if you need them In the Output panel, show output from SonarLint.
- For projects that support PackageReference, copy this XML node into the project file to reference the package.
Hello Folks, today we will explore regarding Top 5 Static code Analysis Tools for Visual Studio, which also includes other 3 Static code Analysis Tools for Visual Studio also as a bonus.
Below are Top 5 Static code Analysis Tools for Visual Studio:
- PVS-Studio
- Kiuwan
- Veracode
- Fortify’s Security Assistant
- Coverity Scan
1. PVS-Studio
PVS-Studio is a tool for detecting bugs and security weaknesses in the source code of programs, written in C, C++, C# and Java. It works under 64-bit systems in Windows, Linux and mac OS environments, and can analyze source code intended for 32-bit, 64-bit and embedded ARM platforms.
It is possible to integrate it into Visual Studio, IntelliJ IDEA, and other widespread IDE. The results of the analysis can be imported into SonarQube.
* Supported languages and compilers

- Windows. Visual Studio 2010-2019 C, C++, C++/CLI, C++/CX (WinRT), C#
- Windows. IAR Embedded Workbench, C/C++ Compiler for ARM C, C++
- Windows. QNX Momentics, QCC C, C++
- Windows/Linux. Keil µVision, DS-MDK, ARM Compiler 5/6 C, C++
- Windows/Linux. Texas Instruments Code Composer Studio, ARM Code Generation Tools C, C++
- Windows/Linux/macOS. GNU Arm Embedded Toolchain, Arm Embedded GCC compiler, C, C++
- Windows/Linux/macOS. Clang C, C++
- Linux/macOS. GCC C, C++
- Windows. MinGW C, C++
- Windows/Linux/macOS. Java
Website Link:PVS-Studio (You can get 30 days trial instead of 7 days trial by using #TechnoThirsty. Send #TechnoThirsty in message box, so you will get 30 days trial.)
2. Kiuwan
Kiuwan is a SAST and SCA platform with the largest technology coverage and integrations in the market.
With a DevSecOps approach, Kiuwan achieves outstanding benchmark scores (Owasp, NIST, CWE, etc) and offers a wealth of features that go beyond static analysis, catering to every stakeholder in the SDLC.
Kiuwan is supporting 30+ programming language and Integrated with different IDEs, Build systems, Bug Trackers and Repositories as shown below:
Website Link = Kiuwan.
3. Veracode
Veracode Static Analysis supports all widely-used languages for desktop, web and mobile applications including:
- Java (Java SE, Java EE, JSP)
- .NET (C#, ASP.NET, VB.NET)
- Web Platforms: JavaScript (including AngularJS, Node.js, and jQuery), Python, PHP, Ruby on Rails, ColdFusion, and Classic ASP
- Mobile Platforms: iOS (Objective-C and Swift), Android (Java), PhoneGap, Cordova, Titanium, Xamarin
- C/C++ (Windows, RedHat Linux, OpenSUSE, Solaris)
- Legacy Business Applications (COBOL, Visual Basic 6, RPG)
Website Link = Veracode
4. Fortify Static Code Analyzer
Fortify’s Security Assistant for Visual Studio 2017 provides real time, as you type code, security analysis and results. It provides structural and configuration analyzers which are purpose built for speed and efficiency to power our most instantaneous security feedback tool. Find vulnerabilities just by writing code and we will help you prevent costly security mistakes. Leveraging the Visual Studio native interface, Security Assistant displays security errors alongside Visual Studio errors and provides Details, Recommendations, from our rich Fortify rule set shared also by Fortify SCA.
VISIT Microsoft’s Visual Studio marketplace to find the Fortify Security Assistant extension and install it into Visual Studio: Fortify Security Assistant for Visual Studio
Website Link = Micro Focus Fortify Static Code Analyzer
5. Coverity
Coverity Scan is an open-source cloud-based tool. It works for projects written using C, C++, Java C# or JavaScript. This tool provides a very detailed and clear description of the issues which helps in faster resolution. A good choice if you are looking for an open-source tool.
Website Link = Coverity By a Synopsys Company
I want you guys to look into below tools as well as a bonus tools.
1. Visual Studio 2019 Code analysis
2. FxCop analyzers in Visual Studio
Installation guide for FxCop analyzer in Visual Studio
3. SonarLint
Website Link=SonarLint
Related Posts:
Sonarlint For Visual Studio 2019 Full
.NET Compiler Platform (Roslyn) Analyzers inspect your C# or Visual Basic code for style, quality, maintainability, design, and other issues. This inspection or analysis is done during design time in all open files.
Analyzers can be divided into the following groups:
Code style analyzers are built in to Visual Studio. The diagnostic ID, or code, for these analyzers is of the format IDExxxx, for example, IDE0067. You can configure preferences in the text editor options page or in an EditorConfig file. Starting in .NET 5.0, code style analyzers are included with the .NET SDK and can be strictly enforced as build warnings or errors. For more information, see here.
Code quality analyzers are now included with the .NET 5 SDK and enabled by default. The diagnostic ID, or code, for these analyzers is of the format CAxxxx, for example, CA1822. For more information, see Overview of .NET code quality analysis.
Third party analyzers can be installed as a NuGet package or a Visual Studio extension. Third party analyzers, such as StyleCop, Roslynator, XUnit Analyzers, and Sonar Analyzer.
Severity levels of analyzers
Each analyzer has one of the following severity levels:
| Severity (Solution Explorer) | Severity (EditorConfig file) | Build-time behavior | Editor behavior |
|---|---|---|---|
| Error | error | Violations appear as Errors in the Error List and in command-line build output, and cause builds to fail. | Offending code is underlined with a red squiggle and marked by a small red box in the scroll bar. |
| Warning | warning | Violations appear as Warnings in the Error List and in command-line build output, but do not cause builds to fail. | Offending code is underlined with a green squiggle and marked by a small green box in the scroll bar. |
| Info | suggestion | Violations appear as Messages in the Error List, and not at all in command-line build output. | Offending code is underlined with a gray squiggle and marked by a small gray box in the scroll bar. |
| Hidden | silent | Non-visible to user. | Non-visible to user. The diagnostic is reported to the IDE diagnostic engine, however. |
| None | none | Suppressed completely. | Suppressed completely. |
| Default | default | Corresponds to the default severity of the rule. To determine what the default value for a rule is, look in the Properties window. | Corresponds to the default severity of the rule. |
Sonarlint Integration With Visual Studio 2019
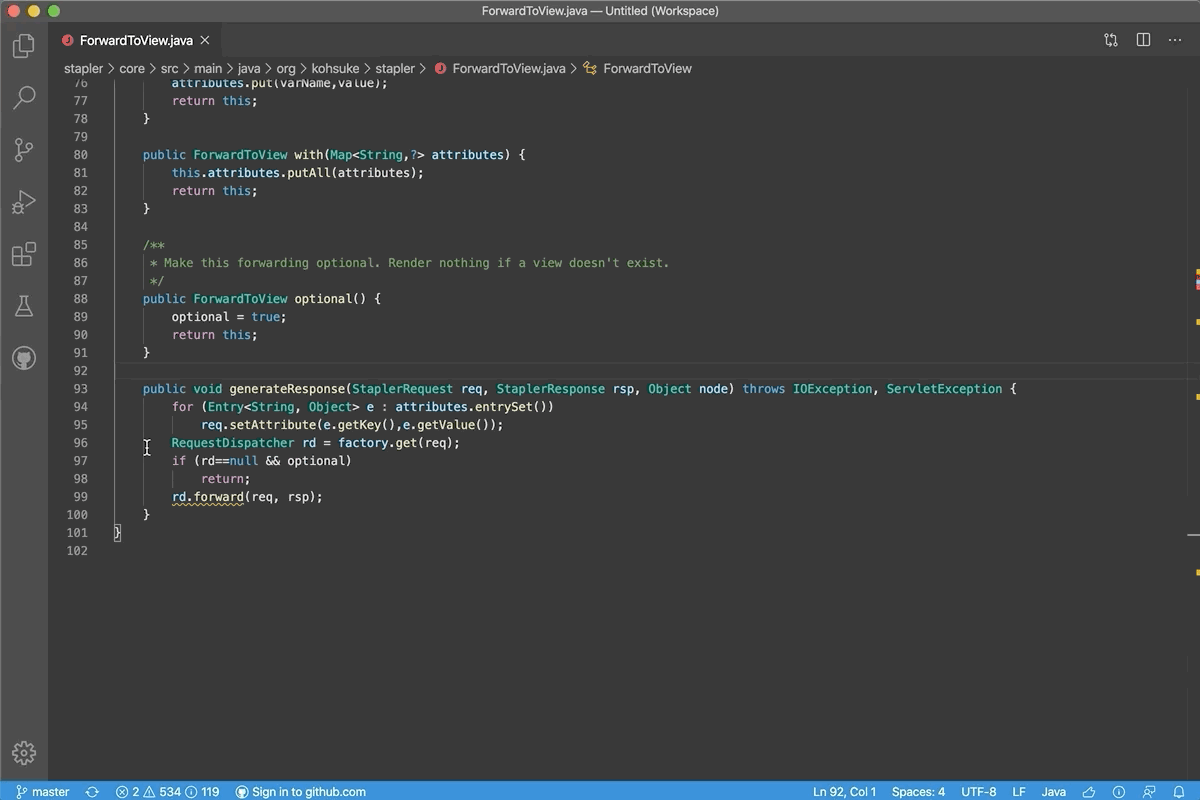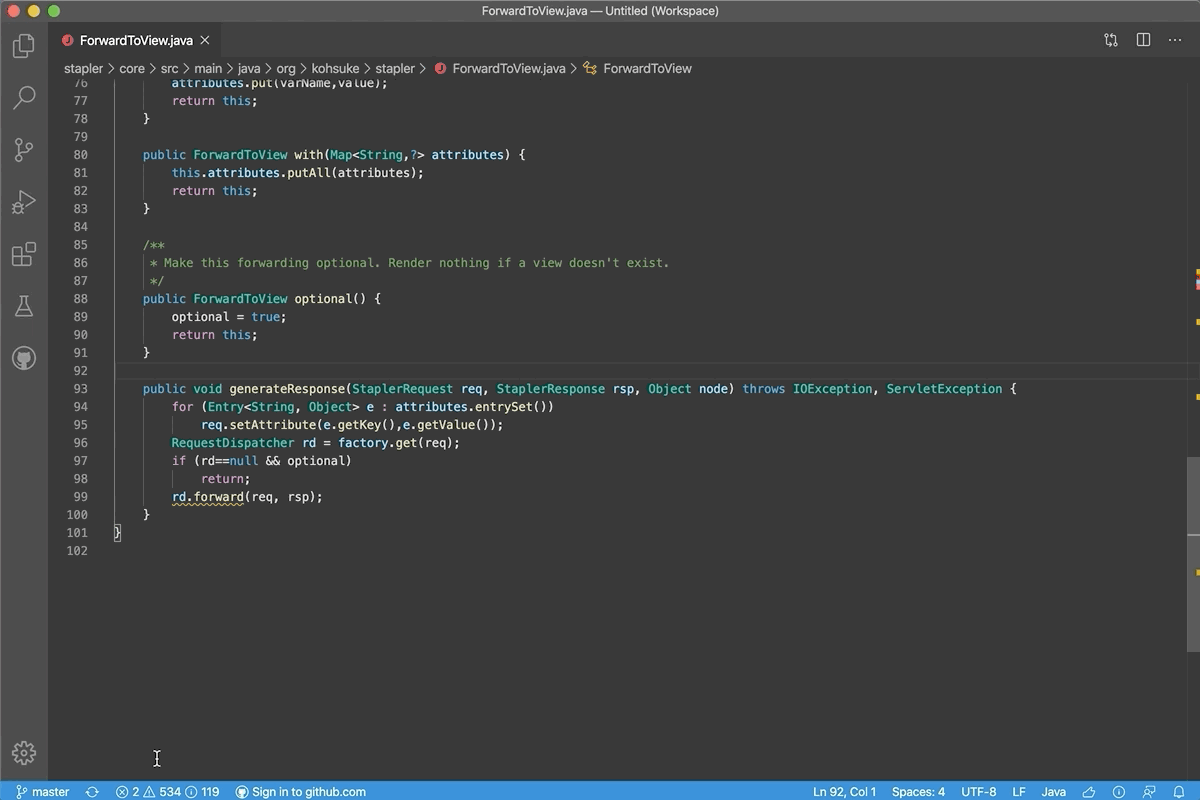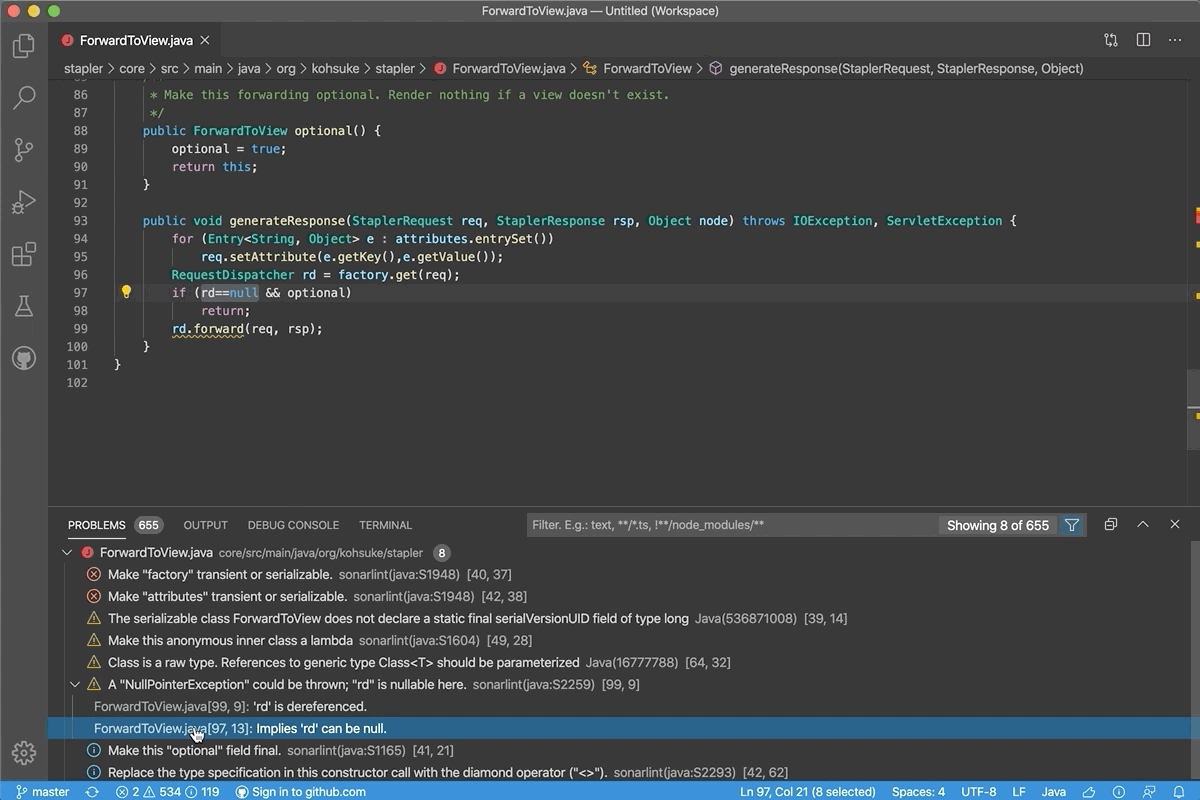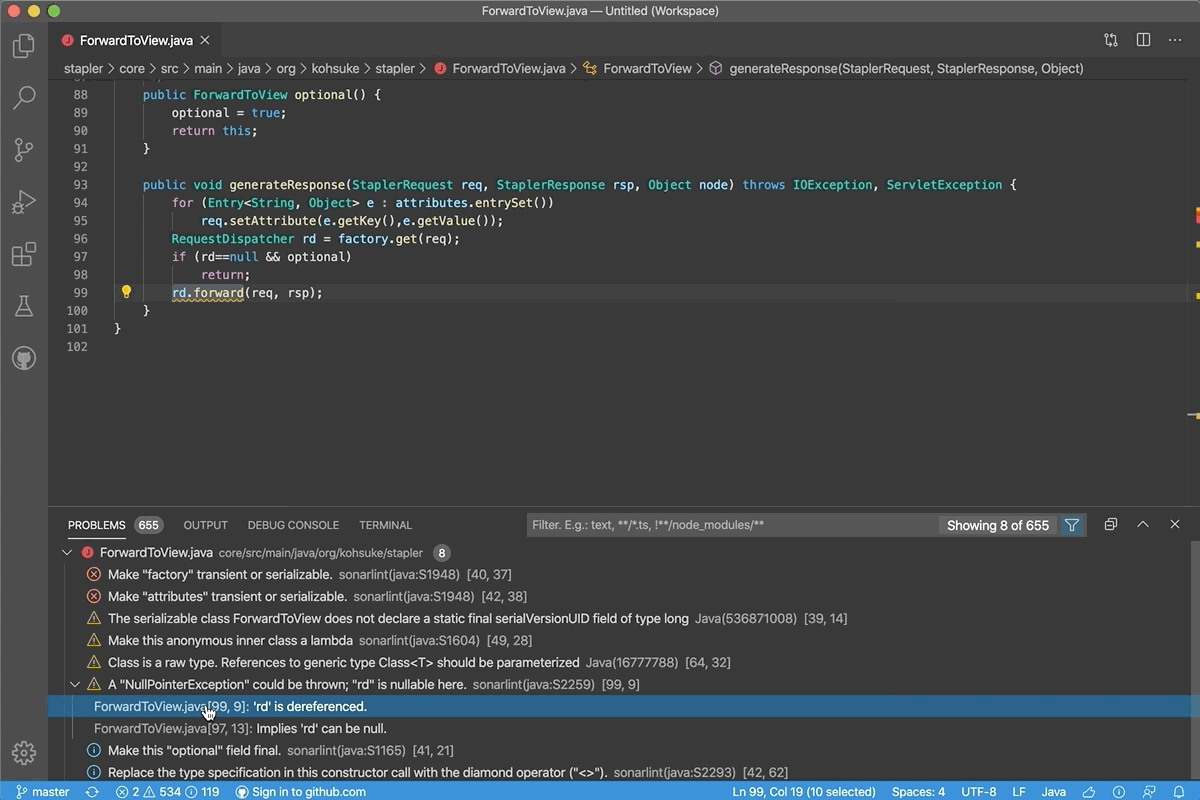
If rule violations are found by an analyzer, they're reported in the code editor (as a squiggle under the offending code) and in the Error List window.

The analyzer violations reported in the error list match the severity level setting of the rule. Analyzer violations also show up in the code editor as squiggles under the offending code. The following image shows three violations—one error (red squiggle), one warning (green squiggle), and one suggestion (three grey dots):
Many analyzer rules, or diagnostics, have one or more associated code fixes that you can apply to correct the rule violation. Code fixes are shown in the light bulb icon menu along with other types of Quick Actions. For information about these code fixes, see Common Quick Actions.
Configure analyzer severity levels
You can configure the severity of analyzer rules, or diagnostics, in an EditorConfig file or from the light bulb menu.
Analyzers can also be configured to inspect code at build time and live as you type. You can configure the scope of live code analysis to execute for the current document only, all open documents, or the entire solution. See How to: Configure the scope of live code analysis.
Tip
Build-time errors and warnings from code analyzers are shown only if the analyzers are installed as a NuGet package. The built-in analyzers (for example, IDE0067 and IDE0068) never run during build.
NuGet package versus VSIX extension
Sonarlint Visual Studio 2019 Configuration
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/11651051/ULTRAMAN_Vertical_Teaser_PRE_US.jpg)
Third party analyzers can be installed per-project via a NuGet package. Some are also available as a Visual Studio extension, in which case they apply to any solution you open in Visual Studio. There are some key behavior differences between these two methods of installing analyzers.
Scope
If you install analyzers as a Visual Studio extension, they apply at the solution level and to all instances of Visual Studio. If you install the analyzers as a NuGet package, which is the preferred method, they apply only to the project where the NuGet package was installed. In team environments, analyzers installed as NuGet packages are in scope for all developers that work on that project.
Build errors
To have rules enforced at build time, including through the command line or as part of a continuous integration (CI) build you can choose from one of the following options:
Create a .NET 5.0 project which includes analyzers by default in the .NET SDK. Code analysis is enabled, by default, for projects that target .NET 5.0 or later. You can enable code analysis on projects that target earlier .NET versions by setting the EnableNETAnalyzers property to true.
Install analyzers as a NuGet package. Analyzer warnings and errors don't show up in the build report if you install the analyzers as an extension.
The following image shows the command-line build output from building a project that contains an analyzer rule violation:
Rule severity

You cannot configure the severity of rules from analyzers that were installed as a Visual Studio extension. To configure rule severity, install the analyzers as a NuGet package.
Next steps
See also
