Attackers can exploit vulnerable XML processors if they can upload XML or include hostile content in an XML document, exploiting vulnerable code, dependencies or integrations.
- Owasp Xxe Prevention
- CWE-611: Information Exposure Through XML External Entity Reference
- XML External Entity (XXE) Processing | OWASP
- Owasp Xxe Cheat Sheet
Welcome to the official repository for the Open Web Application Security Project® (OWASP) Cheat Sheet Series project. The project focuses on providing good security practices for builders in order to secure their applications. In order to read the cheat sheets and reference them, use the project's official website. The very first OWASP Prevention Cheat Sheet, the Cross Site Scripting Prevention Cheat Sheet, was inspired by RSnake’s XSS Cheat Sheet, so we can thank RSnake for our inspiration. Dec 03, 2019 XML External Entity (XXE) Injection Payload list. In this article, we will explain what XML external entity injection is, and their common examples, explain how to find and exploit various kinds of XXE injection, and summarize how to prevent XXE injection attacks.
Attacks
Applications and in particular XML-based web services or downstream integrations might be vulnerable to attack if:
- The application accepts XML directly or XML uploads, especially from untrusted sources, or inserts untrusted data into XML documents, which is then parsed by an XML processor.
- Any of the XML processors in the application or SOAP based web services has document type definitions (DTDs) enabled. As the exact mechanism for disabling DTD processing varies by processor, it is good practice to consult a reference such as the OWASP Cheat Sheet ‘XXE Prevention’.
- If the application uses SAML for identity processing within federated security or single sign on (SSO) purposes. SAML uses XML for identity assertions, and may be vulnerable.
- If the application uses SOAP prior to version 1.2, it is likely susceptible to XXE attacks if XML entities are being passed to the SOAP framework.
Being vulnerable to XXE attacks likely means that the application is vulnerable to denial of service attacks including the Billion Laughs attack

Defenses
Developer training is essential to identify and mitigate XXE. Besides that, preventing XXE requires:
Owasp Xxe Prevention

- Whenever possible, use less complex data formats such as JSON, and avoiding serialization of sensitive data.
- * Patch or upgrade all XML processors and libraries in use by the application or on the underlying operating system. Use dependency checkers. Update SOAP to SOAP 1.2 or higher.
- * Disable XML external entity and DTD processing in all XML parsers in the application, as per the OWASP Cheat Sheet ‘XXE Prevention’.
- * Implement positive (“whitelisting”) server-side input validation, filtering, or sanitization to prevent hostile data within XML documents, headers, or nodes.
- * Verify that XML or XSL file upload functionality validates incoming XML using XSD validation or similar.
- * SAST tools can help detect XXE in source code, although manual code review is the best alternative in large, complex applications with many integrations.
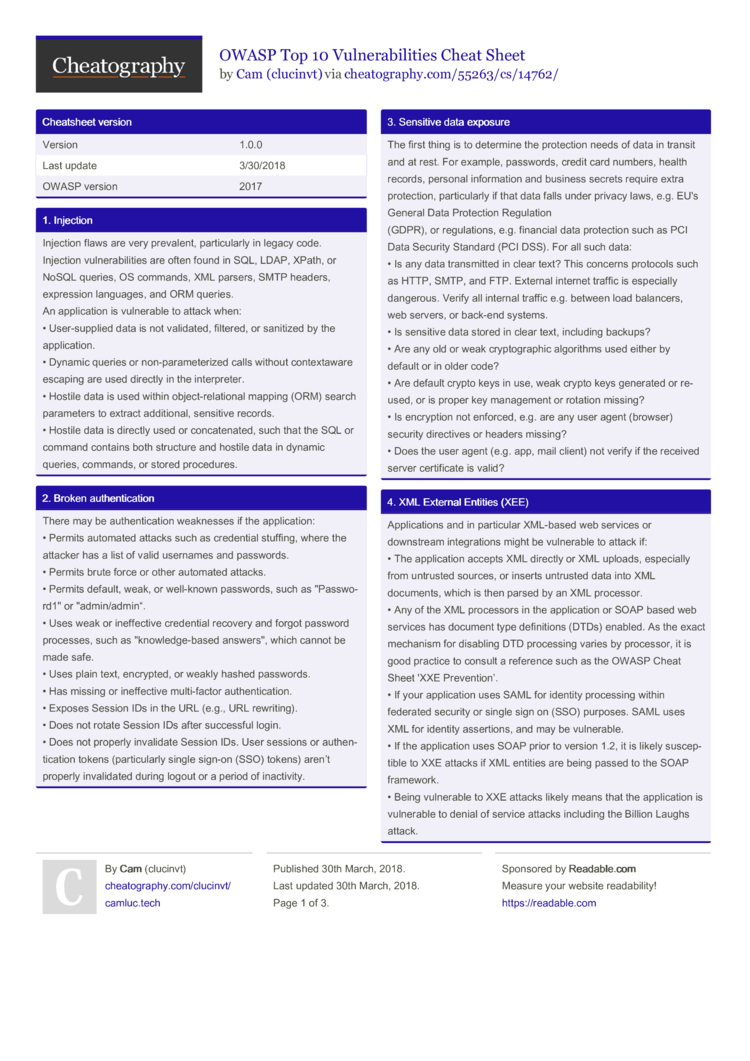
If these controls are not possible, consider using virtual patching, API security gateways, or Web Application Firewalls (WAFs) to detect, monitor, and block XXE attacks.
Note: OWASP expects to complete the next major update of its Top Ten project sometime this year. And it’s considering a number of new contenders that have risen in prominence over the past 3-4 years. Follow us here for an update as soon as OWASP Top Ten 2021 officially drops. As of our post date, OWASP is still looking for input from the application security industry. Share your perspective here.
When managing a website, it’s important to stay on top of the most critical security risks and vulnerabilities. The OWASP Top 10 is a great starting point to bring awareness to the biggest threats to websites in 2021.
What is OWASP?
OWASP stands for the Open Web Application Security Project, an online community that produces articles, methodologies, documentation, tools, and technologies in the field of web application security.
CWE-611: Information Exposure Through XML External Entity Reference
What is the OWASP Top 10?
OWASP Top 10 is the list of the 10 most common application vulnerabilities. Macbook pro iso download. It also shows their risks, impacts, and countermeasures. Updated every three to four years, the latest OWASP vulnerabilities list was released in 2017. Let’s dive into it!
XML External Entity (XXE) Processing | OWASP
The Top 10 OWASP vulnerabilities in 2021 are:
- Injection
- Broken Authentication
- Sensitive Data Exposure
- XML External Entities (XXE)
- Broken Access control
- Security misconfigurations
- Cross Site Scripting (XSS)
- Insecure Deserialization
- Using Components with known vulnerabilities
- Insufficient logging and monitoring
Owasp Xxe Cheat Sheet
Stop OWASP Top 10 Vulnerabilities